Deploy Your Way
Stealth Networking for a Zero-Trust World
A flexible, cloud-native solution or a deployable software fabric for existing infrastructure.

Dynamic Multi-Path Stealth Networking
Unlike traditional VPNs or SD-WANs, Dispersive splits, encrypts, and routes traffic across multiple unpredictable paths—making interception virtually impossible while ensuring ultra-resilient connectivity.
Eliminate Attack Surfaces
Built with zero-trust principles, Dispersive hides network endpoints, eliminates single points of failure, and enforces least-privilege access—neutralizing cyber threats before they even begin.
.png?width=87&height=85&name=Zero-Trust%20Enclaves%20for%20Data%20Sovereignty%20and%20Compliance-v2%20(1).png)
High-Performance, Scalable Connectivity
Whether securing cloud, hybrid, or edge environments, Dispersive optimizes network performance with low-latency, high-speed encryption—ensuring security never slows you down.
The convenience of the cloud
DispersiveCloud
DispersiveCloud is a hosted solution that brings the power of Dispersive’s groundbreaking network fabric while simplifying the deployment and management process without compromising on performance or security. We operate on state-of-the-art cloud networks, partnering with Amazon Web Services and Azure.
Self-host for more control & complexity
DispersiveFabric
DispersiveFabric is our robust, flexible solution designed for larger, more complex environments. A software-defined overlay network, DispersiveFabric utilizes a microservices architecture to provide unparalleled security, reliability, and performance. Deployable on any type of infrastructure with infinite scale- public cloud, private cloud, containers, VMs, dedicated hardware.
.jpg?width=912&height=912&name=iStock-1361547059%20(1).jpg)
Dispersive Stealth Networking Multi-Path/Multi-Cloud: Step by Step
Step 1
Split-Session Multipath
Data streams are split at the authenticated source and re-addressed with a Dispersive header to force traffic to follow different network paths based on instructions from the Dispersive Controller across one or more physical circuits.
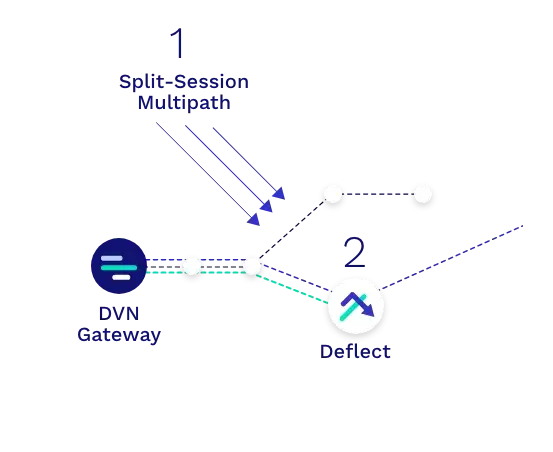
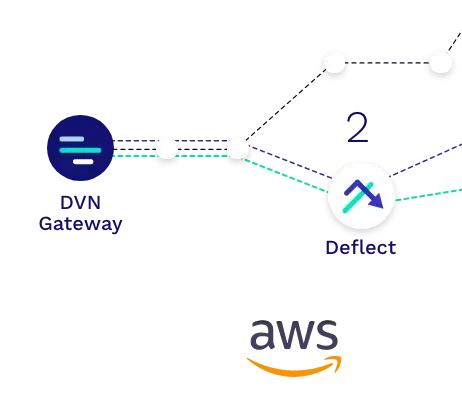
Step 2
Data Deflections
The underlying IP networks deliver these packets to Dispersive software nodes known as Data Deflects. Placement of these deflects influences the actual physical paths traversed.
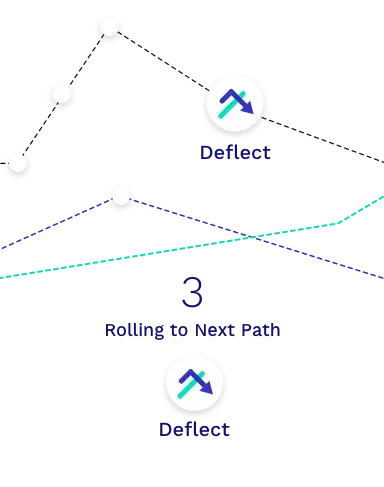
Step 3
Rolling to Next Path
New paths can be established/rolled during the transmission enhancing performance by avoiding link failures and bypassing congested pathways.
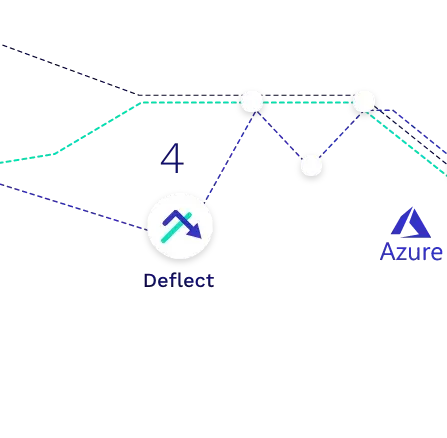
Step 4
Deflections Re-Address Packets
The deflects receive the packets and re-address them for the final destination.
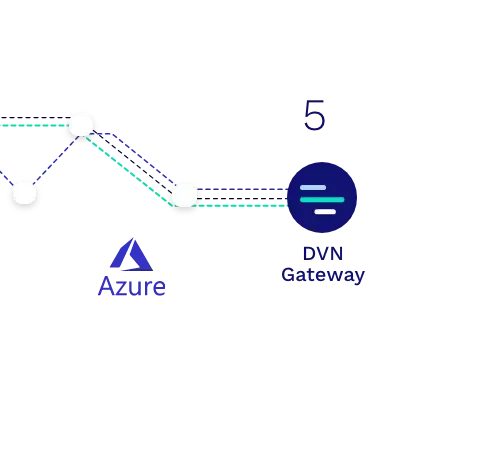
Step 5
Data Reassembled
The authenticated destination reassembles the split packet streams and strips out the Dispersive header information before passing the original packet to the receiving application. Missing packets are re-requested to ensure guaranteed packet delivery.
Stealth Networking: The Future of Secure, Unstoppable Cloud Connectivity
Traditional network perimeters are obsolete—leaving organizations exposed and constrained by outdated security models. Stealth Networking redefines secure cloud-edge connectivity, making your network invisible to attackers while delivering unmatched resilience and efficiency.
Seamlessly replacing legacy WAN technologies, Stealth Networking eliminates the vulnerabilities of IPSec tunnels and the complexity of managing multiple connections. Whether you're transitioning to the cloud or optimizing a multi-cloud environment, our stealth-based approach ensures superior performance, airtight security, and cost-effective scalability—without trade-offs.
Move faster, stay secure, and eliminate attack surfaces. With Stealth Networking, cloud adoption is no longer a risk—it’s an advantage.
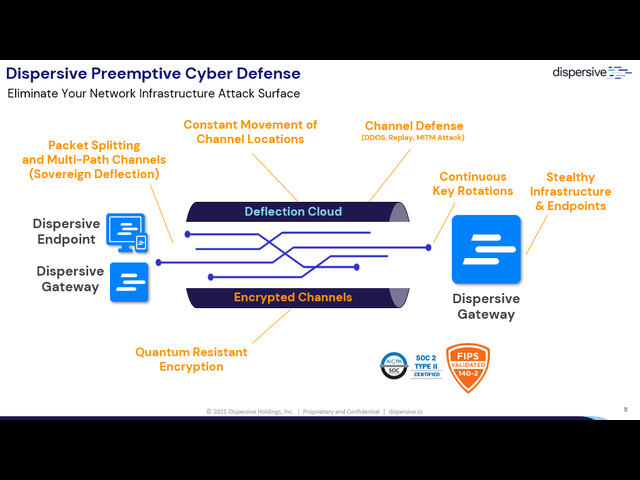
How It Works: Preemptive Cyber Defense In Action
The Dispersive Platform is built for resilience, performance, and reliability in the most demanding network environments. Combining our deflection cloud, endpoint software, Zero Trust gateways, and egress gateways, we create an invisible, multi-path transport layer that preemptively neutralizes threats before they reach your network.
With Layer 2–4 transport, our technology ensures fail-safe operations, dynamic routing, and elegant failure resistance—delivering up to 10x better performance, 20% lower latency, and seamless connectivity even under attack.
Stay ahead of threats. Stay connected. Stay secure.
FAQs
Dispersive goes beyond VPNs and SD-WANs by using dynamic multi-path networking, which splits, encrypts, and transmits data across multiple unpredictable routes. This approach eliminates single points of failure, mitigates interception risks, and ensures high-performance, resilient connectivity.
Unlike IPSec tunnels, which create static, predictable paths vulnerable to attacks, Dispersive’s networking technology obfuscates and disperses traffic across multiple pathways. This makes it nearly impossible for adversaries to detect, intercept, or compromise sensitive data.
Yes! DispersiveCloud provides a cloud-native deployment for seamless integration into hybrid and multi-cloud environments, while DispersiveFabric can be deployed as software within existing infrastructure, offering flexible adoption without requiring a full network overhaul.
Dispersive’s multi-path, adaptive routing technology optimizes traffic flow in real time, balancing security with speed. By continuously assessing network conditions, Dispersive delivers low-latency, high-speed encryption without sacrificing security, making it ideal for mission-critical workloads.
Dispersive is purpose-built for industries that require uncompromising security and resilience, including defense, intelligence, critical infrastructure, financial services, healthcare, and cloud-based enterprises. Any organization that needs zero attack surface networking with high availability will benefit from Dispersive’s technology.
