CrowdStrike + Dispersive
Setting the New Standard for Adaptive, Identity-Aware Networking
Continuous Authorization and Real-Time Threat Containment
Extend CrowdStrike Falcon protection into the network with adaptive, identity-aware security that stops breaches before they begin.

Patient Zero Isolation
Automatically segment or isolate risky users and devices before lateral movement begins.

Insider & Impersonation Threat Defense
Prevent impersonation-based attacks and insider risk across employees, contractors, and vendors.

Adaptive Zero Trust Enforcement
Continuously adjust access privileges with real-time risk scoring to strengthen your Zero Trust posture.
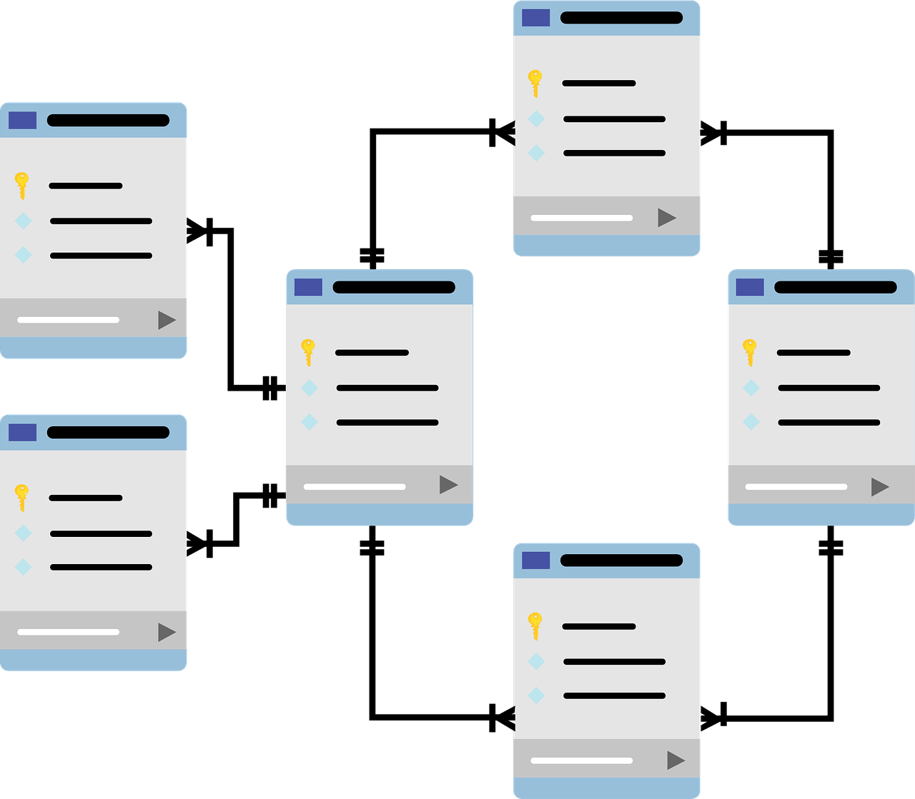
Dispersive Stealth Networking and CrowdStrike have partnered to deliver continuous authorization and real-time threat containment by extending CrowdStrike Falcon® protection into the network layer. The integration unites endpoint, identity, and network intelligence so that when user or device risk scores rise, Dispersive automatically enforces adaptive access and isolation policies.
High-risk endpoints are contained within minutes, while trusted users stay connected, preventing insider threats, impersonation attacks, and lateral movement. Customers benefit from faster containment, safer financial transactions, and greater confidence for SOC and IT teams, with full visibility, overrides, and audit trails built in.
How Enterprises Put Continuous Authorization Into Action
From insider threats to financial transactions, here’s where the joint CrowdStrike–Dispersive solution delivers the most value.
Secure Sensitive Transactions
High-value financial operations require uncompromising protection. The integration between CrowdStrike and Dispersive enforces continuous identity verification and dynamic authorization throughout sensitive workflows. If a user’s risk score rises mid-session, access can be restricted instantly — preventing unauthorized transfers, data exfiltration, or fraud attempts. Financial institutions, like New American Funding, benefit from adaptive controls that safeguard critical transactions while maintaining a smooth user experience for trusted employees and partners.

Insider Threat Prevention
Organizations face growing risks from within, whether through compromised credentials, careless employees, or malicious insiders. By continuously monitoring CrowdStrike Falcon® risk scores and enforcing adaptive network segmentation with Dispersive, enterprises can quickly identify and isolate high-risk behavior. SOC teams gain real-time visibility, while IT administrators retain control with whitelists and overrides. The result is faster containment of insider threats without disrupting legitimate business activity.

Dynamic Zero Trust in Action
Traditional Zero Trust stops at login. The joint CrowdStrike–Dispersive solution takes it further, applying continuous verification across the entire session. Device and identity risk signals are evaluated in real time, with Dispersive dynamically adjusting network and application access. This ensures that access privileges always match current risk posture. Enterprises gain a living Zero Trust model, one that adapts instantly, contains threats before they spread, and strengthens resilience against modern attacks.
Accelerate Investigations and Response

Dispersive and CrowdStrike when deployed together could provide us the ability to potentially see and act on user and device risk in real time. We can look to provide risk-based access to network resources based on zero trust principles. It’s a powerful competitive advantage for us in both security and trust.
Jeff Farinich
SVP Technology & CISO
New American Funding
FAQs
By combining CrowdStrike Falcon risk scores with Dispersive’s dynamic network controls, the system automatically adapts access policies. High-risk entities are segmented or isolated, while trusted devices remain fully operational.
The CrowsdStrike + Dispersive integration extends Zero Trust beyond authentication, continuously verifying risk throughout the session. Access decisions adjust in real time, not just at login.
• SOC analysts gain faster containment and fewer manual actions.
• IT administrators get control, whitelists, and fewer support tickets.
• Enterprises reduce breach risk and build customer trust.
No. With whitelisting, manual override, and transparent logs, SOC and IT teams can prevent false positives from impacting critical systems.
Dispersive® Stealth Networking Solutions
Fortifying Networks with Secure, Resilient, and High-Performance Connectivity
DispersiveCloud™
DispersiveCloud™ is a hosted SAAS SOC 2 Type II-compliant solution that brings the power of our groundbreaking network fabric that simplifies the deployment and management process without compromising performance or security. We operate on state-of-the-art cloud networks, partnering with various vendors, including Amazon Web Services and Azure to enable global high availability.
DispersiveFabric™
DispersiveFabric™ is our robust, flexible solution designed for larger, more complex environments. A software-defined overlay network, DispersiveFabric™ utilizes a microservices architecture to provide unparalleled security, reliability, and performance. Deployable on any type of infrastructure with infinite scale- public cloud, private cloud, containers, VMs, dedicated hardware.
.jpg?width=912&height=912&name=iStock-1361547059%20(1).jpg)
Key Capabilities
The integration brings together endpoint, identity, and network intelligence to contain threats before they spread. Patient Zero Isolation proactively detects and isolates risky behavior at the very first sign of compromise. With On-Demand Endpoint Isolation, teams can instantly segment or disconnect devices showing elevated risk. Dynamic Authorization ensures access rights adjust continuously in real time, while Granular Policy Enforcement applies precise, score-based controls to protect sensitive networks and applications. Together, these capabilities deliver faster containment and stronger Zero Trust protection without disrupting trusted users.
Ready to See Continuous Authorization in Action?
Learn how CrowdStrike + Dispersive can stop breaches before they begin.
